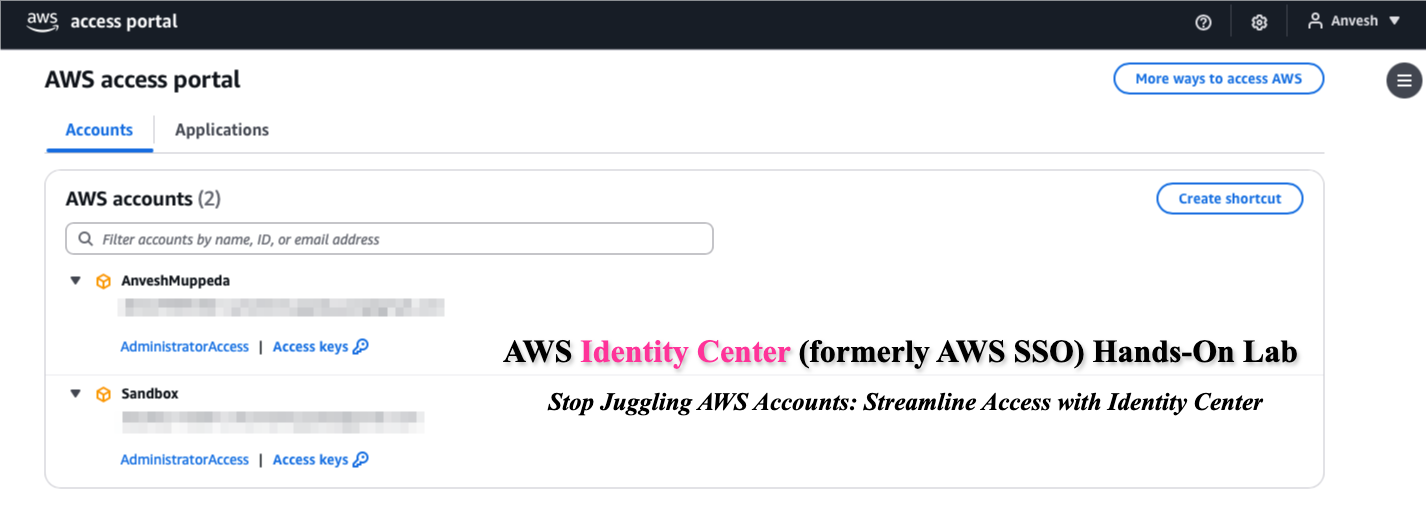
AWS Identity Center (formerly AWS SSO) Hands-On Lab
Stop Juggling AWS Accounts: Streamline Access with Identity Center
Overview
This hands-on lab provides a comprehensive, step-by-step guide to setting up and using AWS Identity Center (formerly AWS Single Sign-On) for managing access to AWS accounts and applications. By completing this lab, you will have a fully functional AWS Identity Center setup that streamlines user access management across your AWS environment.
Prerequisites
- An AWS account with administrative privileges
- Basic understanding of AWS services and IAM concepts
- Access to the AWS Management Console
Learning Objectives
After completing this lab, you will be able to:
- Enable and configure AWS Identity Center
- Create users and groups in AWS Identity Center
- Set up permission sets with appropriate access levels
- Assign users and groups to AWS accounts
- Create and manage multiple AWS accounts within an organization
- Test and validate access through the AWS access portal
Part 1: Initial Setup and Configuration
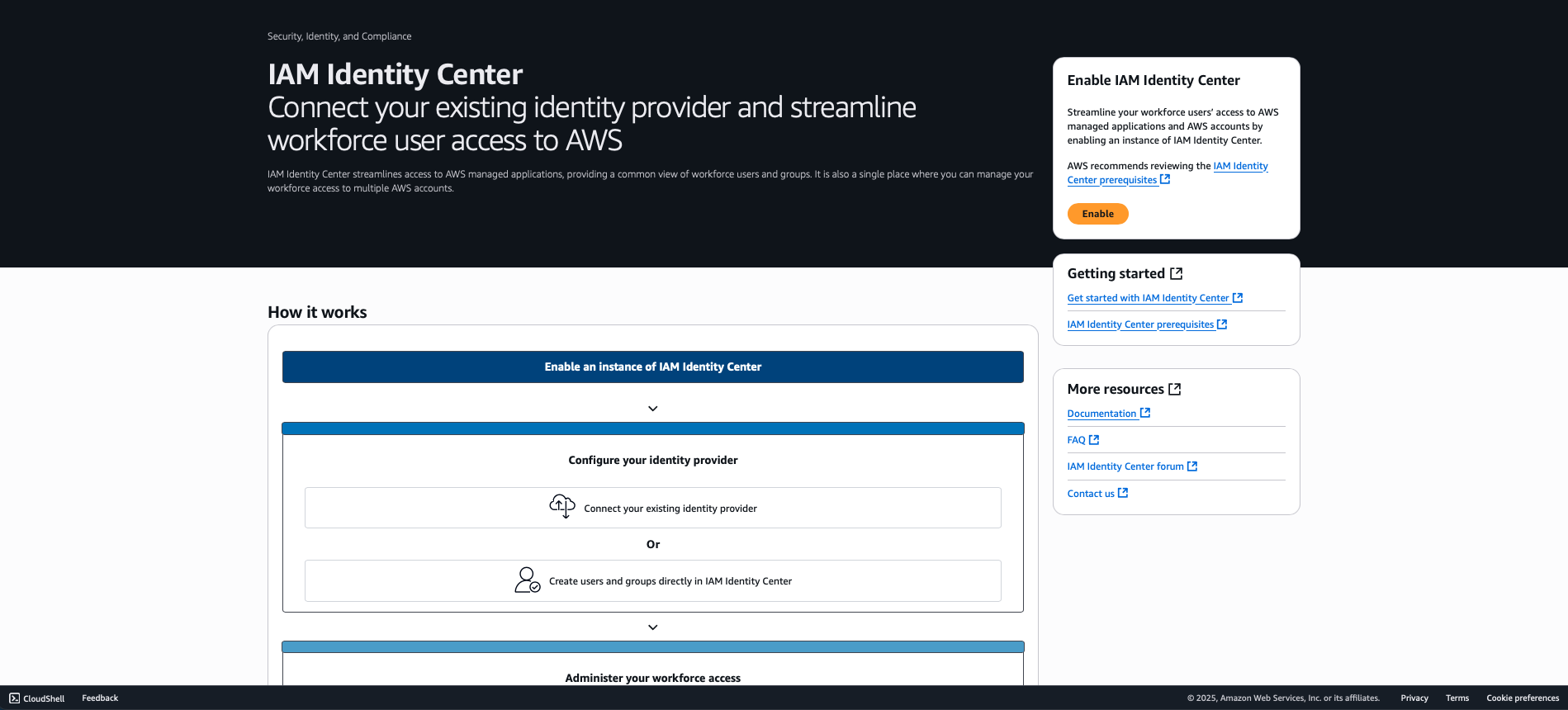
Step 1: Enable AWS Identity Center
- Sign in to the AWS Management Console with administrative privileges
- Navigate to AWS Identity Center service
- Select the us-east-1 region (Note: AWS Identity Center can only be enabled in one region per organization)
- Click Enable AWS Identity Center
Step 2: Verify AWS Identity Center Setup
- Confirm that AWS Identity Center is successfully enabled
- Note the automatically generated AWS access portal URL (format:
https://d-xxxxxxxxxx.awsapps.com/start) - Record this URL as you'll need it for user access later
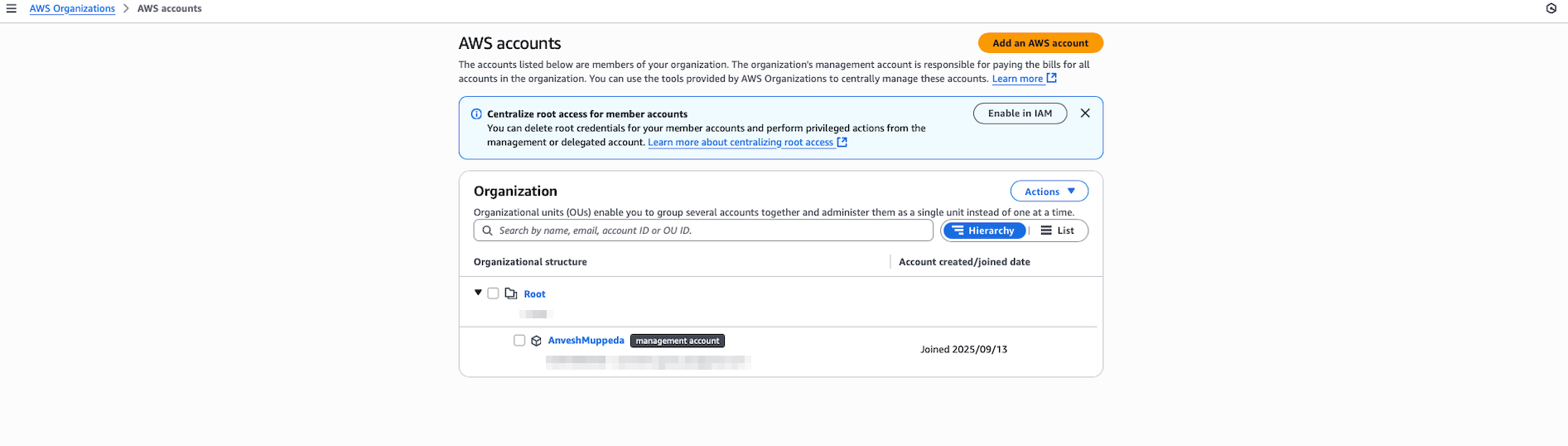
Step 3: Verify AWS Organizations Creation
- Navigate to AWS Organizations in the console
- Verify that an organization has been automatically created
- Confirm your current account is set as the management account
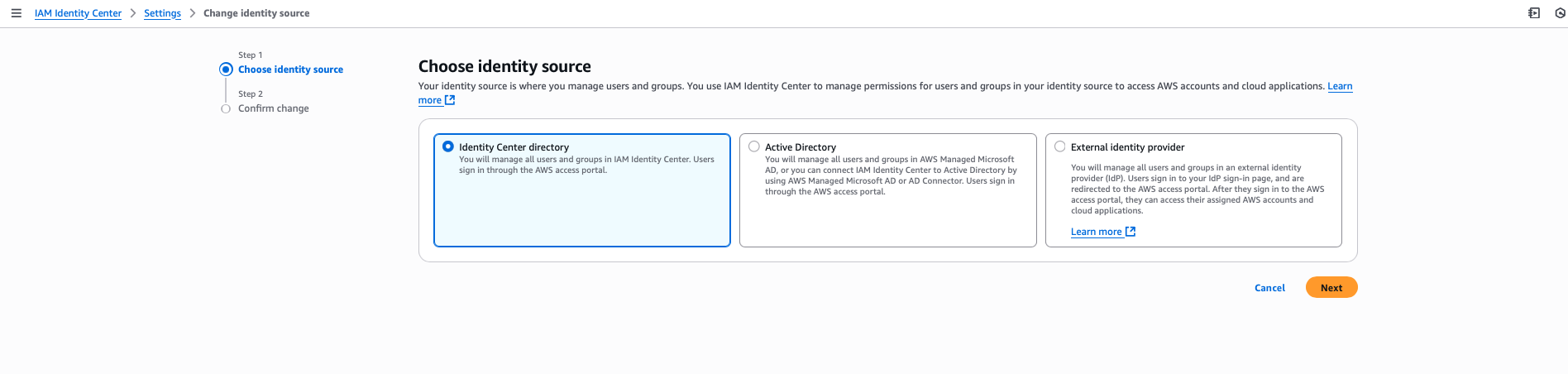
Step 4: Configure Identity Source
- In AWS Identity Center, navigate to Settings → Identity source
- Verify the default identity source is set to "AWS Identity Center"
- Note: This allows you to create users and groups directly within AWS Identity Center
Alternative Options: You can connect external identity providers such as Microsoft Active Directory or SAML 2.0 compatible IdPs. However, changing the identity source will delete all existing AWS Identity Center users and groups.
Part 2: User and Group Management
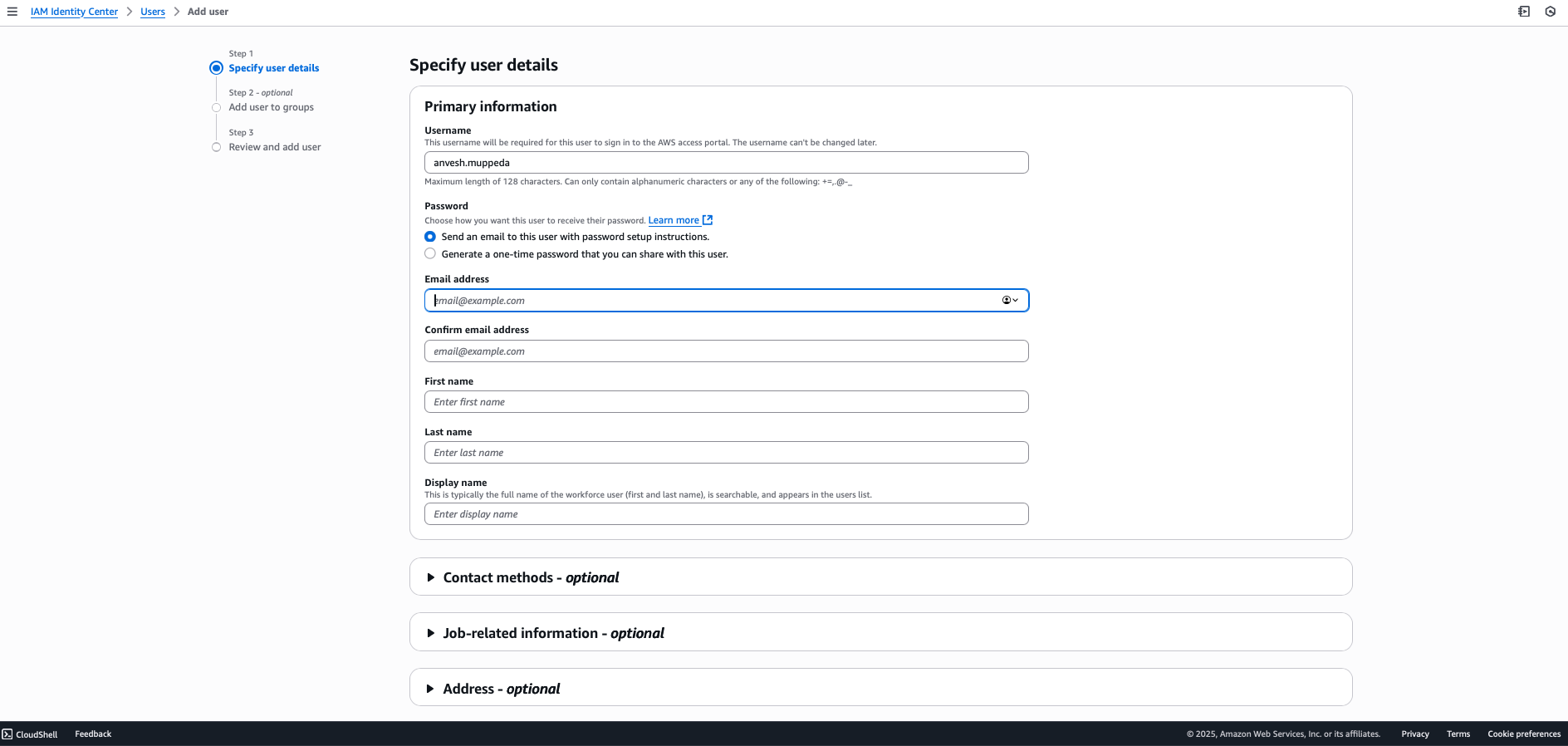
Step 5: Create Your First User
- Navigate to Users in the AWS Identity Center console
- Click Add user
- Fill in the user details:
- Username:
anvesh.muppeda(or your preferred username) - Email address: Enter a valid email
- First name and Last name: Fill as appropriate
- Username:
- Click Next and review the details
- Click Add user
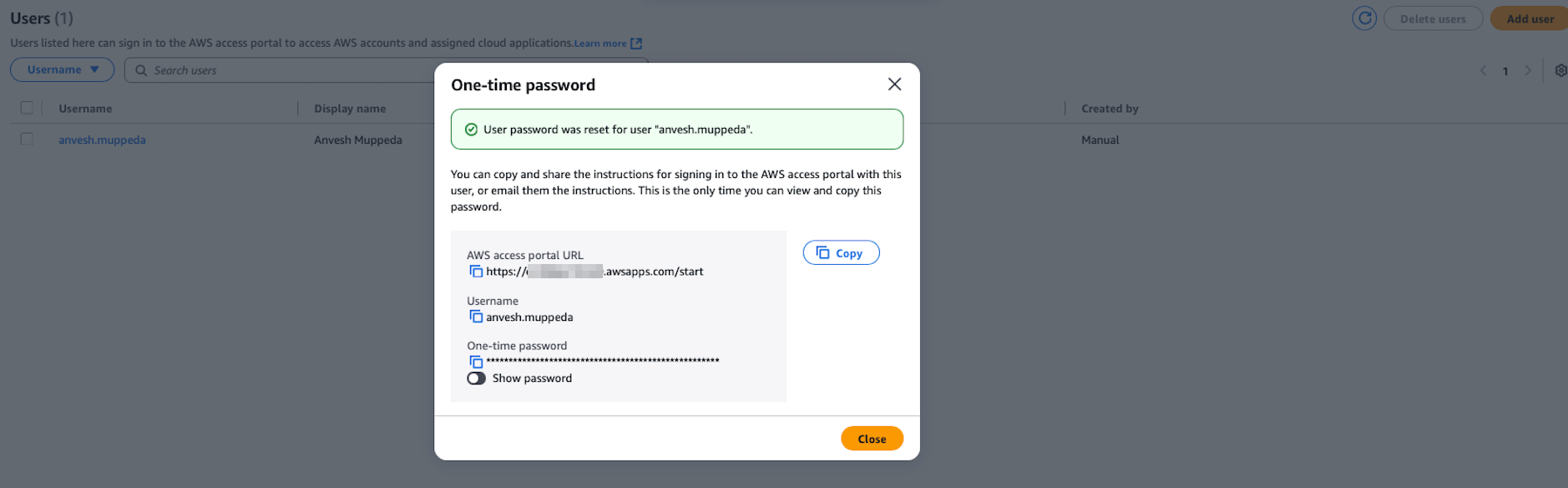
Important Information Captured:
- AWS access portal URL:
https://d-xxxxxxxxxx.awsapps.com/start - Username:
anvesh.muppeda - One-time password: (auto-generated, can be changed during first login)
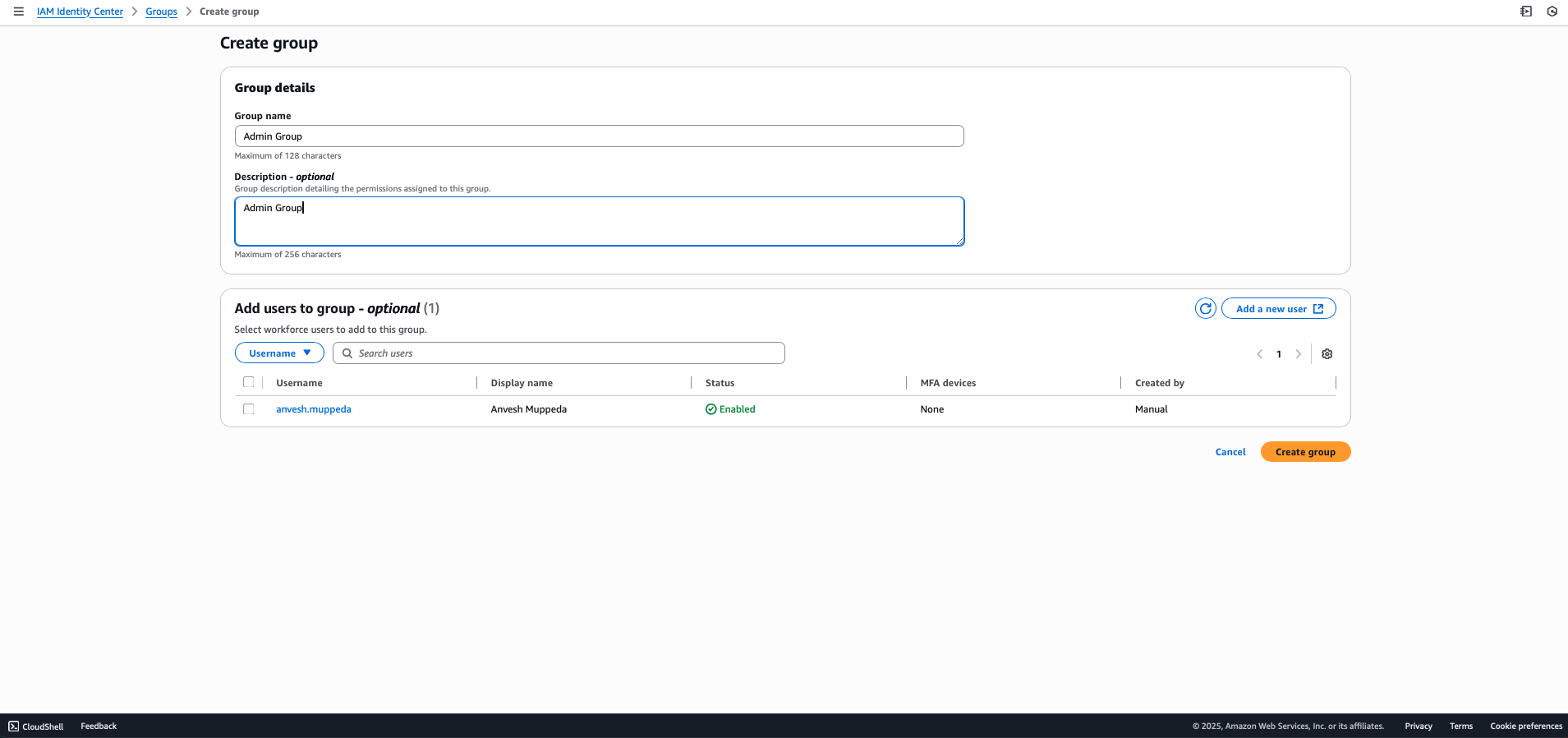
Step 6: Create an Admin Group
- Navigate to Groups in the AWS Identity Center console
- Click Create group
- Enter group details:
- Group name:
Admin - Description:
Administrator group with full access privileges
- Group name:
- Click Create group
- Select the newly created Admin group
- Click Add users to group
- Select the user created in Step 5 (
anvesh.muppeda) - Click Add users
Part 3: Permission Sets and Access Management
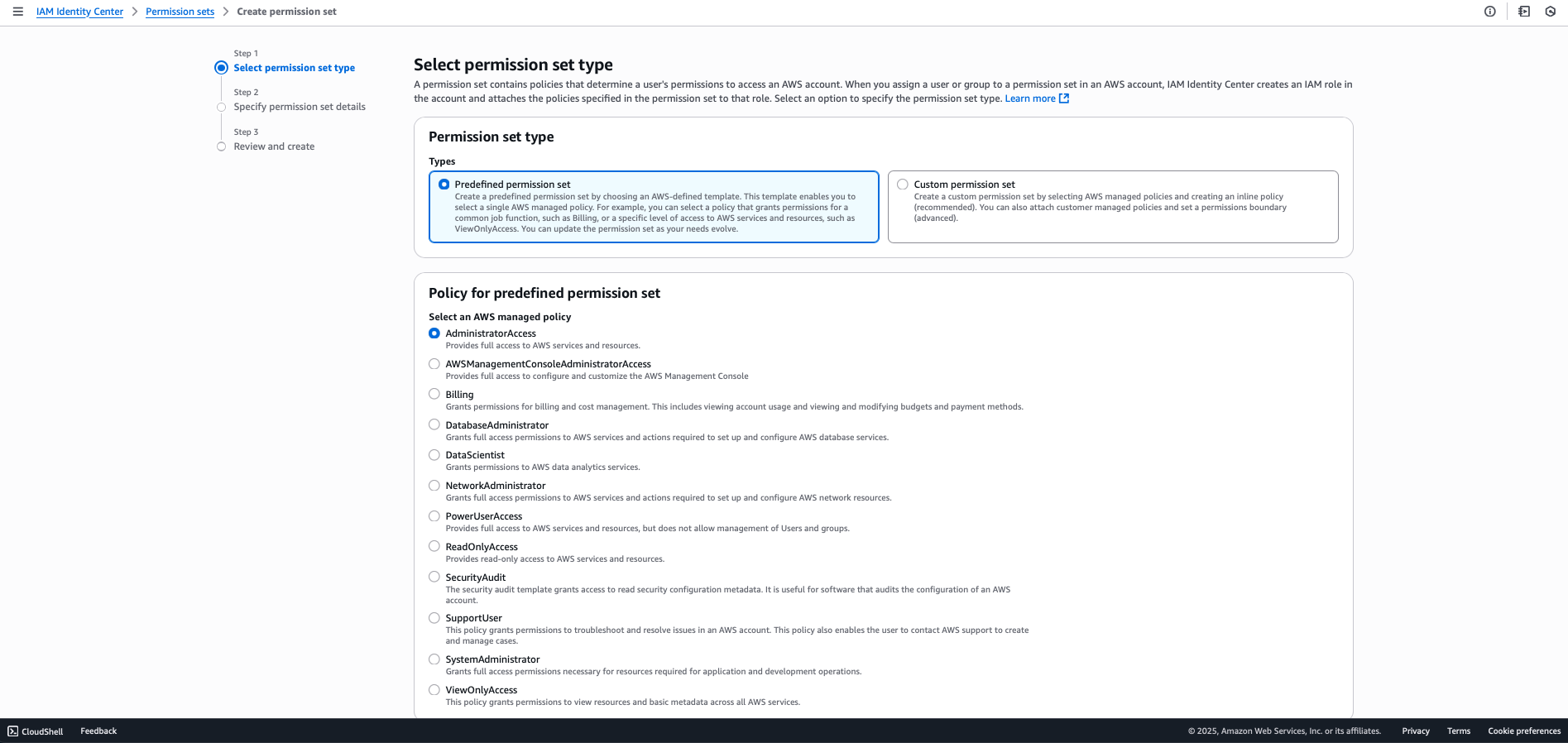
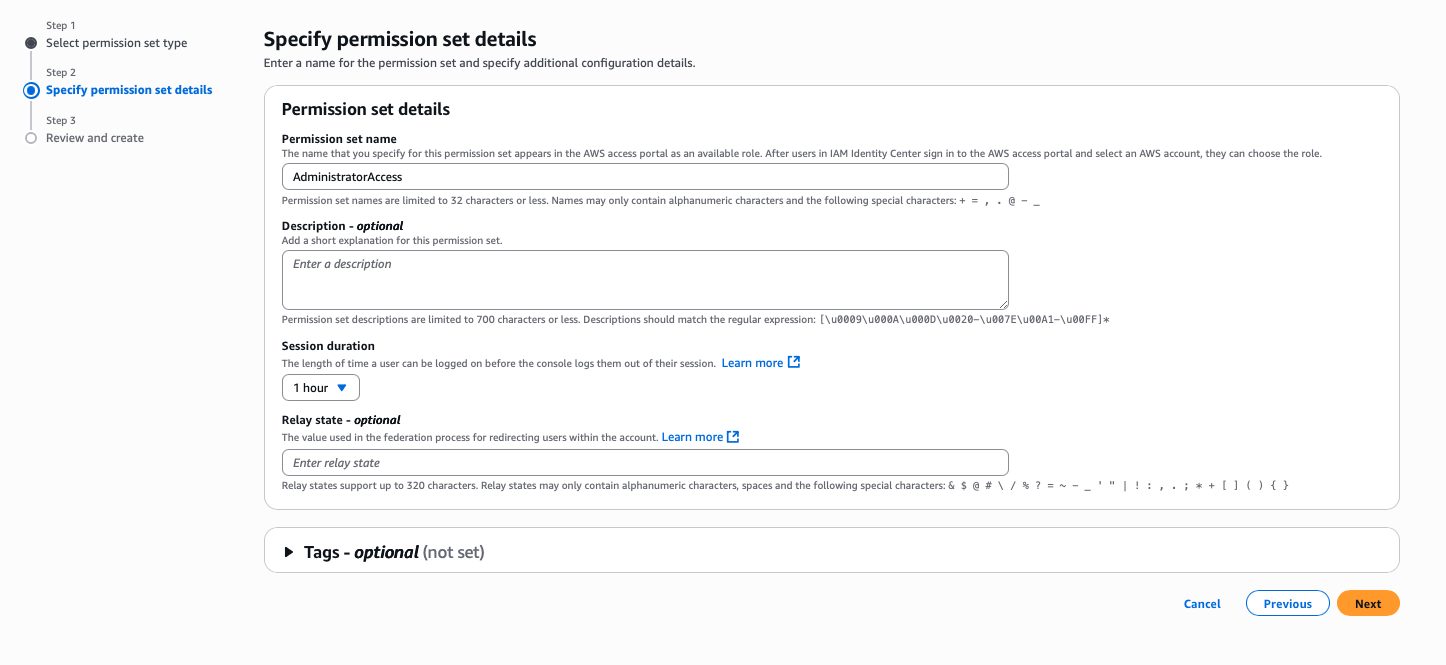
Step 7: Create an Admin Permission Set
- Navigate to Permission sets in the AWS Identity Center console
- Click Create permission set
- Select Predefined permission set
- Choose AdministratorAccess from the dropdown
- Configure session duration:
- Default: 1 hour
- Maximum: 12 hours (adjust as needed for your security requirements)
- Click Next and review the configuration
- Click Create
Step 8: Assign Account Access
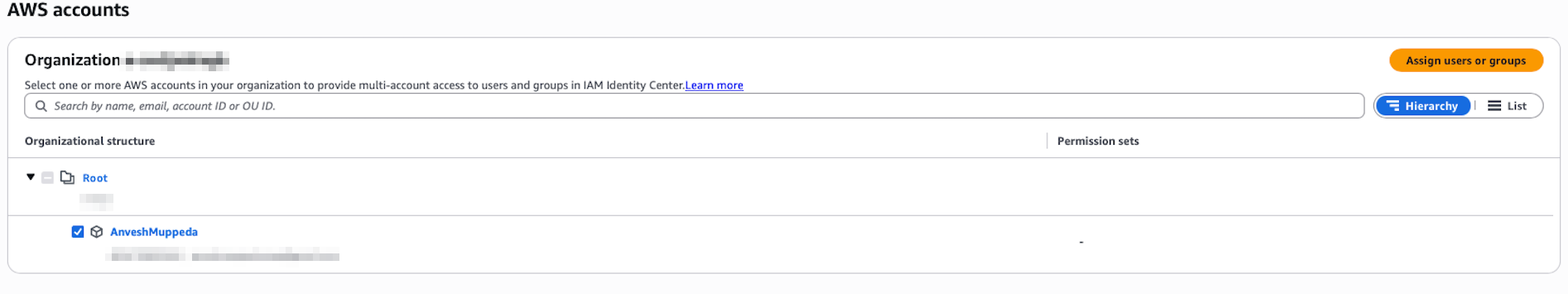
- Navigate to AWS accounts in the AWS Identity Center console
- Select your management account
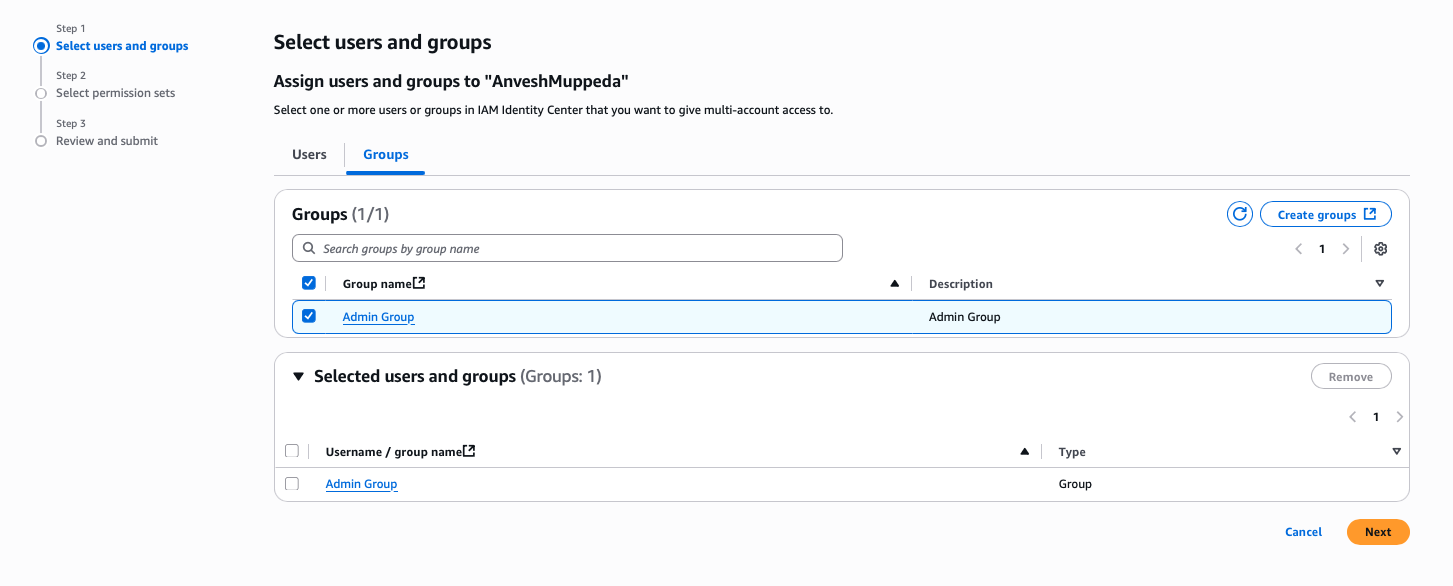
- Click Assign users or groups
- On the Users and groups tab, select the Admin group
- Click Next
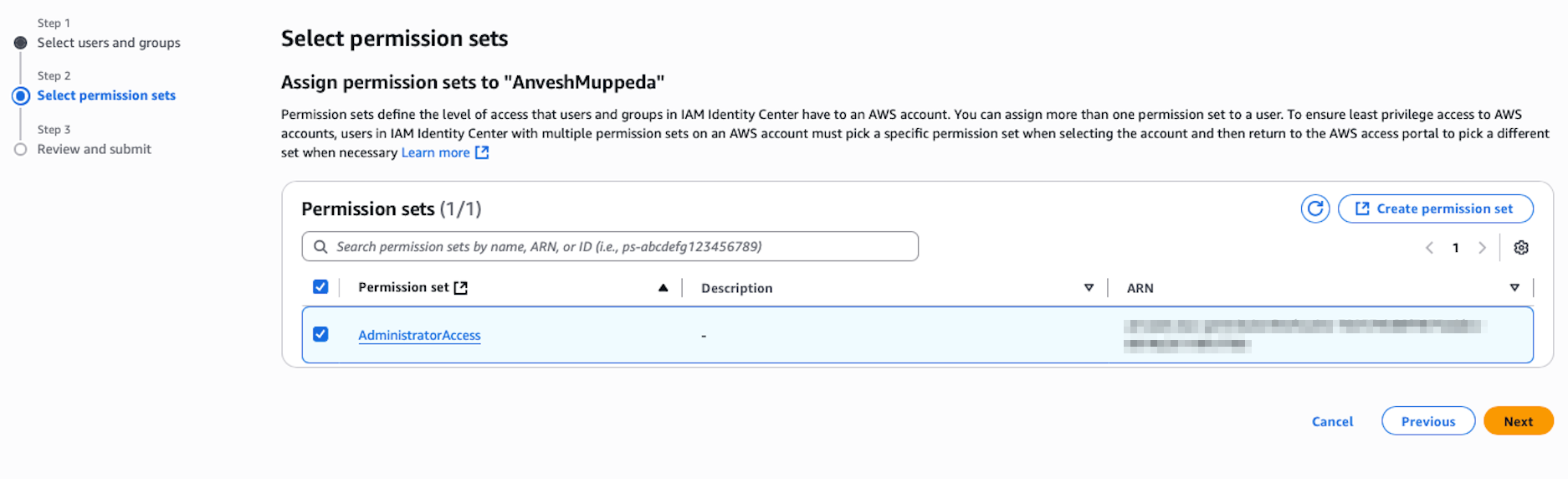
- On the Permission sets tab, select the AdministratorAccess permission set
- Click Next, review the assignment, and click Submit
Part 4: Testing and Validation
Step 9: Test User Access
- Open a new incognito/private browser window
- Navigate to your AWS access portal URL:
https://d-xxxxxxxxxx.awsapps.com/start - Enter the login credentials:
- Username:
anvesh.muppeda - Password: Use the one-time password provided during user creation
- Username:
- First-time login process:
- You'll be prompted to change the password
- Create a strong, secure password
- Complete any additional security setup if prompted
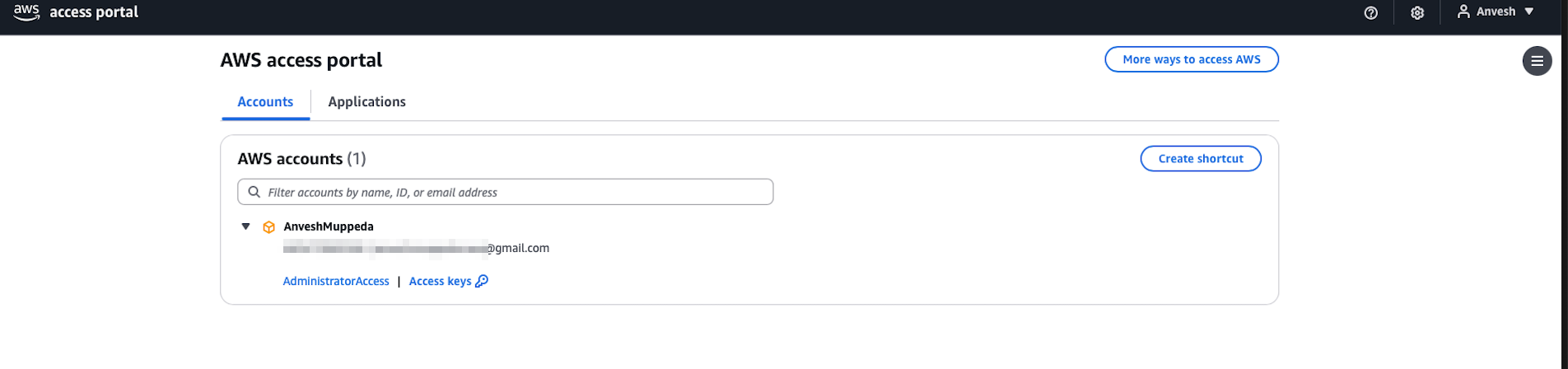
Step 10: Verify Console Access
- After successful authentication, you should see available AWS accounts
- Click on Management account
- Click Management console to access the AWS Management Console
- Verify you have AdministratorAccess permissions by checking various services
Part 5: Expanding Your Organization
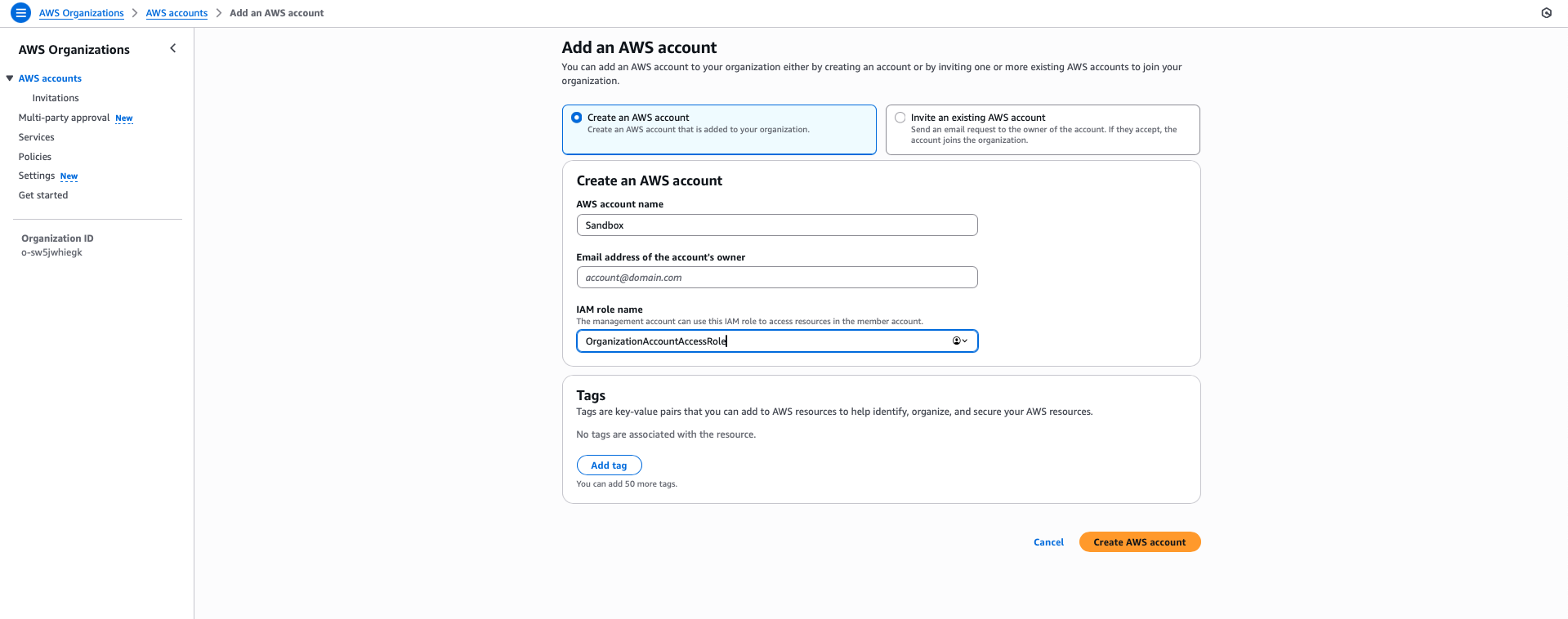
Step 11: Create a New AWS Account
- Navigate to AWS Organizations in the management console
- Click AWS accounts from the left navigation
- Click Add an AWS account
- Select Create an AWS account
- Fill in the required information:
- AWS account name: Choose a descriptive name (e.g., "Development Account")
- Email address: Use a unique email address for this account
- IAM role name: Leave default or customize as needed
- Click Create AWS account
- Wait for the account creation process to complete (this may take a few minutes)
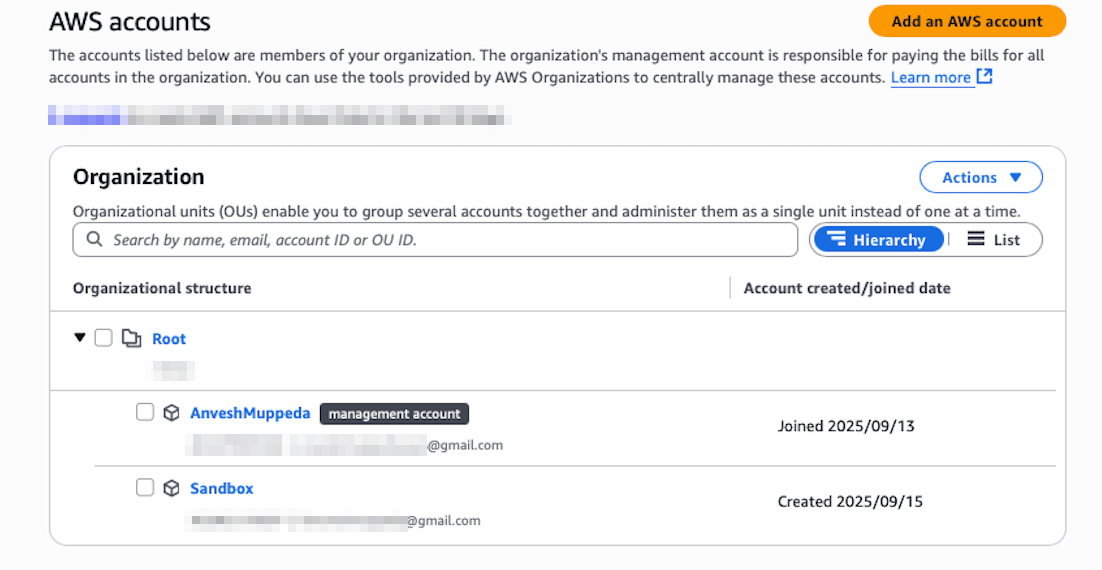
Step 12: Assign Access to the New Account
- Return to AWS Identity Center console
- Navigate to AWS accounts
- Locate and select the newly created AWS account
- Click Assign users or groups
- Select the Admin group
- Click Next
- Select the AdministratorAccess permission set
- Click Next, review, and click Submit
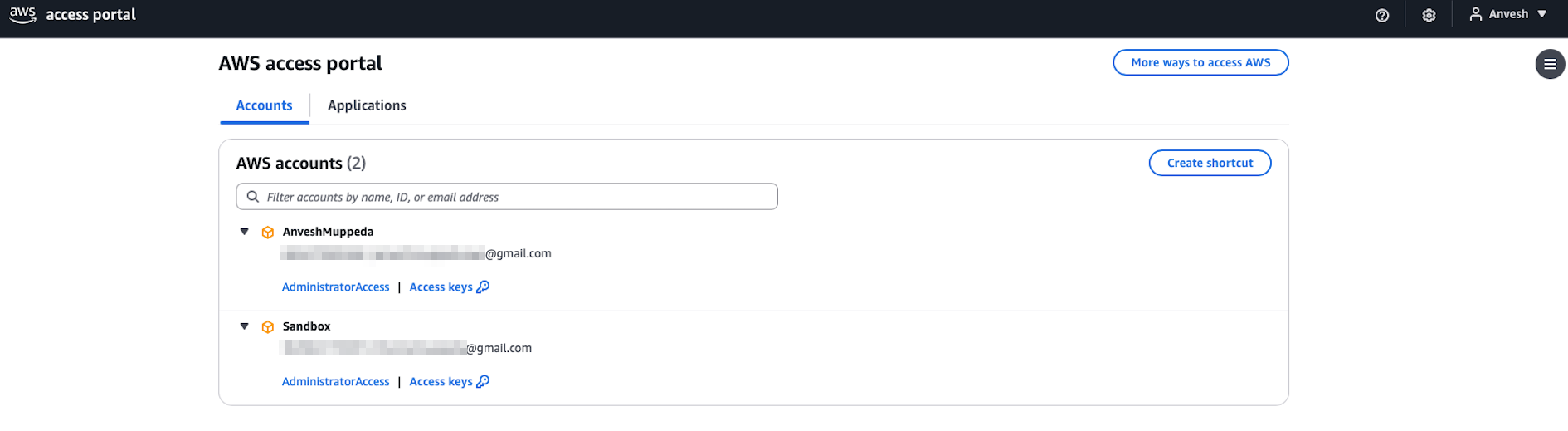
Step 13: Test Multi-Account Access
- Open a new incognito window and navigate to the AWS access portal
- Log in with your user credentials (
anvesh.muppeda) - You should now see both AWS accounts listed:
- Management account
- Your newly created account
- Test access to both accounts by clicking on each and selecting Management console
- Verify you have appropriate permissions in both environments
Best Practices and Security Considerations
User Management
- Use descriptive usernames and group names
- Regularly review and audit user access
- Implement the principle of least privilege
- Set appropriate session durations based on security requirements
Permission Sets
- Create role-based permission sets rather than user-specific ones
- Use AWS managed policies when possible
- Regularly review and update permissions
- Document the purpose of each permission set
Account Organization
- Use descriptive account names that reflect their purpose
- Implement a consistent naming convention
- Consider using organizational units (OUs) for better account grouping
- Set up appropriate service control policies (SCPs) as needed
Troubleshooting Common Issues
Login Problems
- Verify the correct AWS access portal URL
- Ensure the user account is active and assigned to appropriate groups
- Check if password reset is needed
Permission Issues
- Verify permission sets are correctly assigned
- Check if the session has expired
- Confirm the user is a member of the correct groups
Account Access Issues
- Ensure the account is properly assigned to users/groups
- Verify the permission set allows the required actions
- Check AWS Organizations settings for any restrictions
Conclusion
You have successfully set up AWS Identity Center with multi-account access management. This foundation allows you to:
- Centrally manage user identities and access
- Provide secure, role-based access to multiple AWS accounts
- Streamline the user experience with single sign-on capabilities
- Maintain security best practices across your AWS organization
Next Steps
Consider exploring these advanced features:
- Integration with external identity providers
- Custom permission sets for specific roles
- Application assignments for SaaS applications
- Advanced session and access policies
- Automated user provisioning with SCIM
This lab guide provides a solid foundation for AWS Identity Center implementation. Always follow your organization's security policies and compliance requirements when implementing identity management solutions.